Intercept SAP No SSO - Token Retrieval Methods
You can retrieve tokens using the following methods.
Browser
This method launches the Intercept WebGUI to generate a new or obtain an existing token for a given card number. The WebGUI has the option to either copy the token to the clipboard with a single click or download the token to a file. The download to file option from the WebGUI is a different file than the File Transfer Method. The file generated from the browser contains just the single token that was returned on the browser page and you can name the file and save it to any location.
-
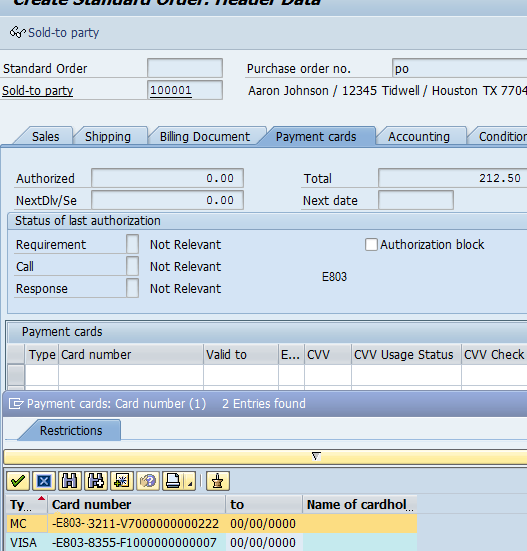
XiSecure Data Intercept parameters configuration is set so that the Browser is the primary transfer method.
-
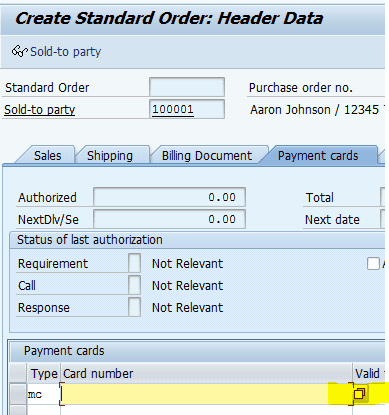
In SAP, whenever the credit card number value is open for entry and you click F4, the WebGUI tokenization screen will be launched. Click F4 or click the drop-down list button to view the value list for the credit card number.
-
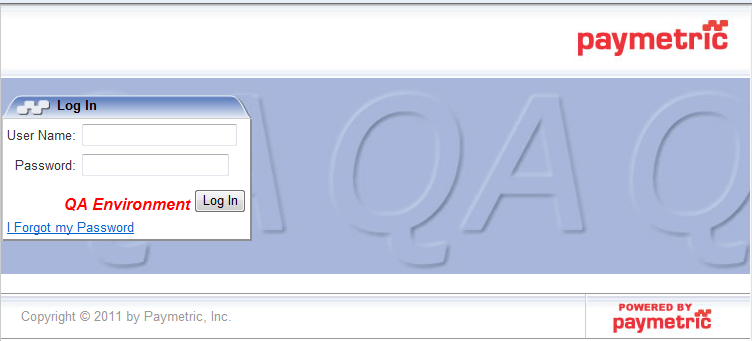
As the PCMA configuration setting is set to Browser, the WebGUI will be launched. Enter the User Name and Password assigned and maintained by your Organization Administrator. Click Log In.
-
The token generation screen is displayed to choose the card type and enter the raw card or token information. Enter the Card type and raw card information on the screen for generation of tokens, and then click Generate Token.
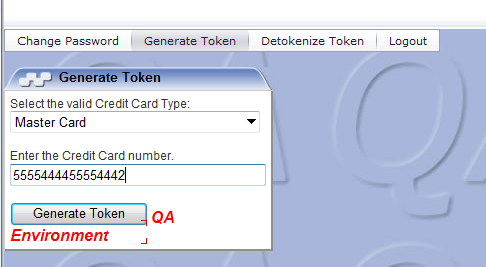
-
The token is generated and you may either copy to clipboard or save to a file.
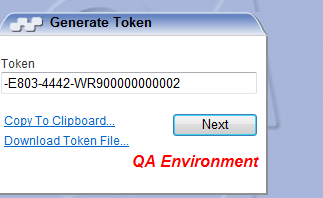
Clipboard
This method places the latest value that is currently in the Windows clipboard into the Payment card field.
-
Once a token is generated and copied to clipboard, it can be pasted (Ctrl-V) for use. This example shows the paste operation on a SAP Customer Master Payment cards tab.
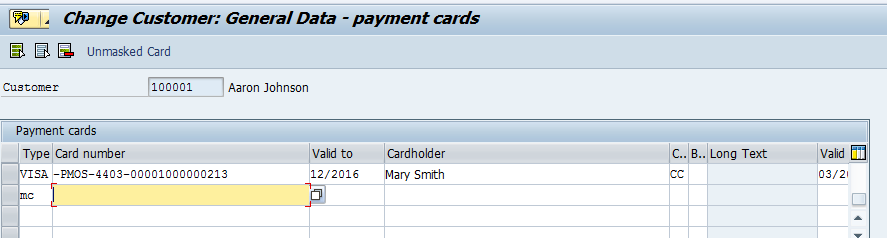
-
Example after the paste operation (Ctrl-V).
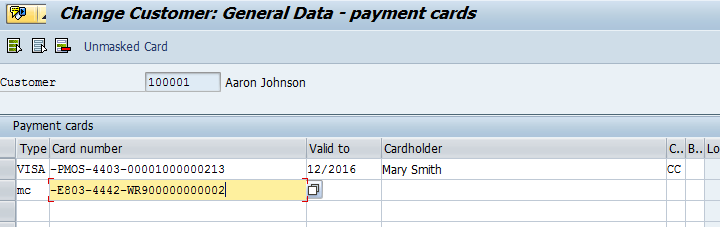
Customer Master
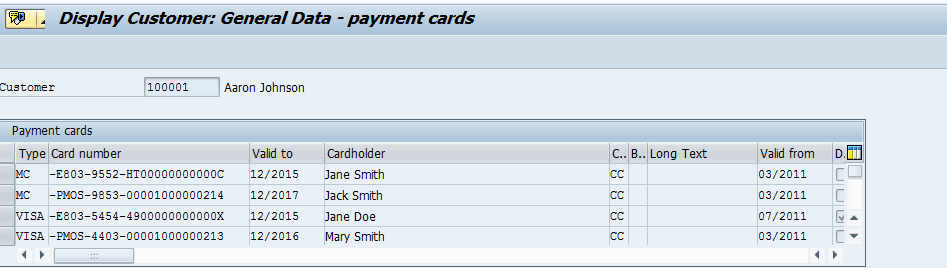
This method provides either a list of tokens from the Customer Master in the Search Help dialogue box or allows you to search for a token in the Customer Master using the last four digits of the card if using the keystroke integration method. Maintaining tokenized payment card numbers on the customer master is a prerequisite. Other (non-default) transfer methods can still be chosen and override the default if the trigger character is utilized.
-
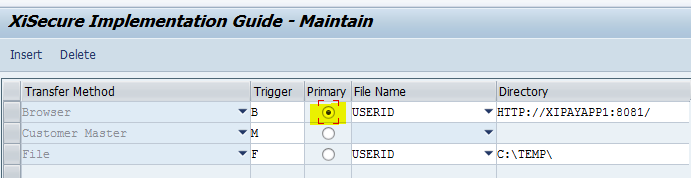
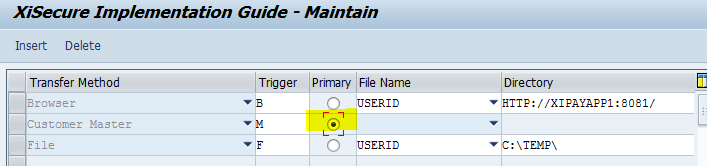
XiSecure Data Intercept parameters configuration is set so the transfer method of Customer Master is the primary trigger.
-
For any authorizations on a sales order or settlement function, click the F4 button or pull down on the help value list to choose from the list of tokens saved for the customer.
-
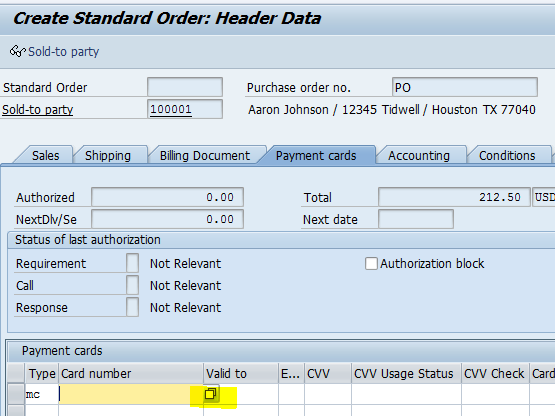
Click the drop-down list in the Card number field, or click F4.
-
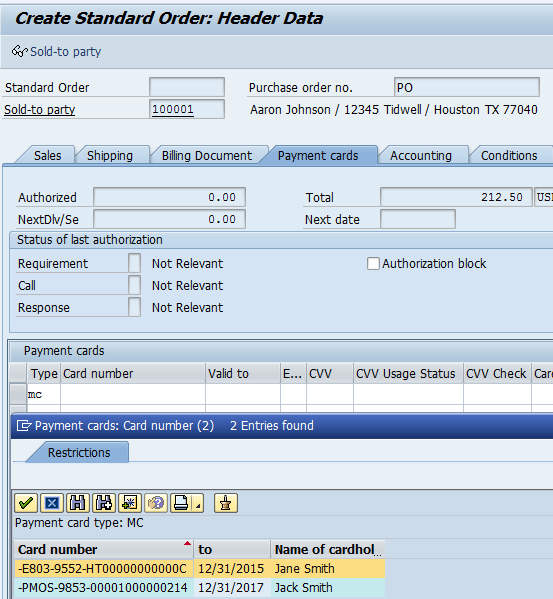
The list of tokens assigned to the Sold to Party (100001) is displayed to choose from.
File
This method opens a defined .txt file that contains a list tokens that were placed in the file by copying and pasting. This can be used to store a list of tokens for commonly used credit cards so you can quickly bring up the list, select the token and continue processing your order. The file naming convention and location is configured by your SAP System Administrator. The standard naming conventions are as follows:
-
USERID.txt (where the SAP User ID is used as the filename)
-
TOKEN.txt
Note that the file naming convention is customizable via the Intercept Parameters Paymetric User Exit (PUE) under XiIntercept Options in the IMG. Simply make a 'Z' or 'Y' version of the /PMENC/PEX_XiIntercept_PARAM Function Module and modify as desired.
-
XiSecure Data Intercept parameters configuration is set so the transfer method of File is the primary trigger. Also note in this example, the file of tokens have to be in the C:\temp\ directory to be uploaded using the filename as userid.txt.
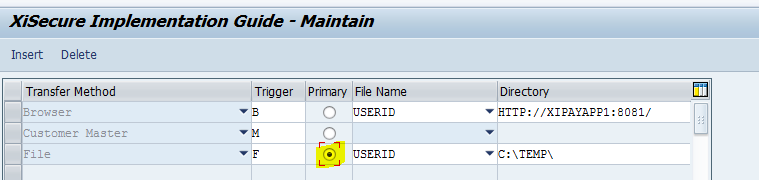
-
The file in this example c:temp\userid.txt contains two tokens.
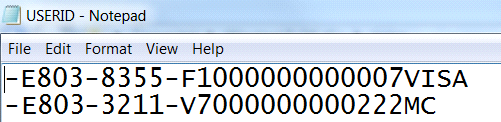
-
Go to VA01 Sales order create. Enter the Sold to Party, Purchase order, material, and quantity.
-
Go to the header of the Sales order by clicking Doc. Header Details.
-
Click the Payment cards tab.
-
Enter the card type and place the cursor on the card number value and click F4. The list of tokens from the file will be proposed for the user to choose from.